Dear attendees, Your are invited tonight at Azotea del Circulo de Bellas Artes from 7.00pm until 9.30pm. Address : Azotea del Círculo de Bellas Artes de Madrid, C. del Marqués de Casa Riera, 2, Centro, 28004 Madrid Please wear your badges, when you arrive go to the main entrance, and tell the security you are here for the Linaro event. You can then get the lift to the last floor.
- Thursday, 16 May 19:00 - 21:30
- Room: Other Venue |
Zaragoza Floor 4
- Wednesday, 15 May 10:15 - 10:35
- Room: AM Coffee Break | Zaragoza I + II
Zaragoza Floor 4
- Thursday, 16 May 10:05 - 10:25
- Room: AM Coffee Break | Zaragoza I + II
Outdoor Terrace - Ground floor, over the bridge
- Tuesday, 14 May 15:35 - 15:55
- Room: PM Coffee Break | Outdoor Terrace - Ground floor, over the bridge
- Wednesday, 15 May 15:20 - 15:45
- Room: PM Coffee Break | Outdoor Terrace - Ground floor, over the bridge
- Thursday, 16 May 15:20 - 15:45
- Room: PM Coffee Break | Outdoor Terrace - Ground floor, over the bridge
Zaragoza Floor 4
- Friday, 17 May 10:00 - 10:20
- Room: AM Coffee Break | Zaragoza I + II
MAD24-100K1 Production-Grade on Arm
Keynote
- Tuesday, 14 May 13:00 - 14:00
- Room: Keynote | Zaragoza III+IV
tbd

Head of Sales at Linaro

VP of Products at Linaro
CTO at Linaro
MAD24-200K3 How ONELab is reshaping Arm at the Edge
Keynote
- Wednesday, 15 May 09:40 - 10:15
- Room: Keynote | Zaragoza III+IV
Today's environment is demanding on Edge and IoT infrastructure. We require high performance platforms, processing vast amounts of data with software and AI that is changing at cloud-native speed, and all must be done safely and securely. To meet these demands, our platforms need to be ready for deployment at scale, have security built-in and enabled by default, and be updatable, adaptable platforms that can host a wide range of workloads. We've risen to these challenges with our work on enabling Arm SystemReady, PSA and PARSEC in open source projects and on devices. Now, we're taking the next step. At this year's Linaro Connect we're pleased to launch ONELab, a new initiative that helps Arm vendors test their platforms for compliance and demonstrate real interoperability between hardware, OSes, and cloud middleware on Arm Edge and Embedded devices. Come and hear from our panel of lead partners how ONELab is transforming the Arm ecosystem.
CTO at Linaro
Senior Principal Edge and IoT Architect at Red Hat
Eng Manager at Texas Instruments
Senior Director Engineering at Qualcomm
Senior Fellow at AMD
Senior Manager at Renesas Electronics Corporation
MAD24-300K2 Arm and Linaro: Accelerating the ecosystem towards Software Defined Vehicles of the future
Keynote
- Thursday, 16 May 09:25 - 09:45
- Room: Keynote | Zaragoza III+IV
In an era where technology is revolutionizing every aspect of our lives, the automotive industry stands at the forefront of innovation. The advent of software-defined vehicles promises a future where cars are not just machines, but intelligent entities that adapt, learn, and evolve. This keynote explores the transformative potential of partnerships in driving this evolution forward. At the heart of this discussion lies the synergy between automotive manufacturers, technology companies, and all stakeholders. By forging strategic partnerships, these entities can leverage their unique expertise to overcome challenges and unlock new opportunities. Together, we can navigate the complexities of developing and implementing software-defined vehicle systems, ensuring seamless integration and optimal performance.

Vice President of Automotive Products, Software and Solutions at Arm
MAD24-300K3 Developer first: Open-Source and Next-Gen AI apps journey continues
Keynote
- Thursday, 16 May 09:45 - 10:05
- Room: Keynote | Zaragoza III+IV
In this talk, we will explore how Qualcomm is embracing open-source software to empower developers and drive innovation in the realm of next-generation AI apps. By prioritizing a developer-first approach, Qualcomm provides comprehensive support, developer-friendly platforms, and collaboration opportunities to foster a vibrant ecosystem. Open-source software is key to accelerating technological advancements and push the boundaries of what is possible. Through partnerships and active engagement with developer communities, we enable developers to leverage open-source tools and resources to create transformative solutions, such as Qualcomm Linux. Join us as we delve into the world of open-source innovation and its impact on shaping the future of AI applications across multiple computing form factors (edge, cloud, mobile).

SVP Engineering at Qualcomm
MAD24-400K1 Architecting for CPU performance on the next phase of AI workloads everywhere on Arm
Keynote
- Friday, 17 May 09:00 - 09:30
- Room: Keynote | Zaragoza III+IV
The expected growth of AI, across every industrial sector, provides unprecedented opportunity for new software capability. Arm’s latest path of innovation for CPU Architecture, through “Scalable Matrix Extensions” (SME), will deliver significant improvements for running such AI and related workloads. Nick Horne will explain the problems SME is solving with an emphasis on software developers and real-world use cases. He will also provide insight into how SME will be enabled in the software ecosystem and how SME will co-exist with dedicated AI accelerators.

VP Engineering, Machine Learning at Arm
A technology showcase where developers are invited to demonstrate the technology they are working on.
This is a fantastic opportunity to see up close what is happening at the very forefront of Arm technology.
List of Demo :
1- Qualcomm Demo : - AI PC with Snapdragon X Elite - rB5 and Open-source robotics - Qualcomm Linux and RB3 Gen 2
2- Qualcomm Landing Team Demo booth : - Qualcomm compute platforms - System Ready and Qualcomm IoT platforms - TensorFlow and AI demo? - OpenCL and Qcom GPU
3- CodeLinaro
4- AudioReach SDK demo
5- FIDO Onboard Device
6- Pixel 6 Upstream Android Development Platform
7- 16K page size with Android
8- ONELab Demo
9- Linaro Automation Appliance
10- sm8x50-userdebug: One AOSP Build to Rule Them All!
11- Debugging and Profiling with Linaro Forge
12- From Setup to Insight: Real-Time Demonstrations of the newest WindowsPerf Tools
13- Linaro Toolchain CI regression detection
14- Almost AArch64 Linux Desktop
15- OP-TEE FF-A notifications in a protected Virtual Machine
16- Project Orko: VirtIO on Xen
Plan: https://drive.google.com/file/d/1OVo6czUwdxclRpPD7diwzAXtxO_EcnFX/view?usp=sharing Toledo Floor 3
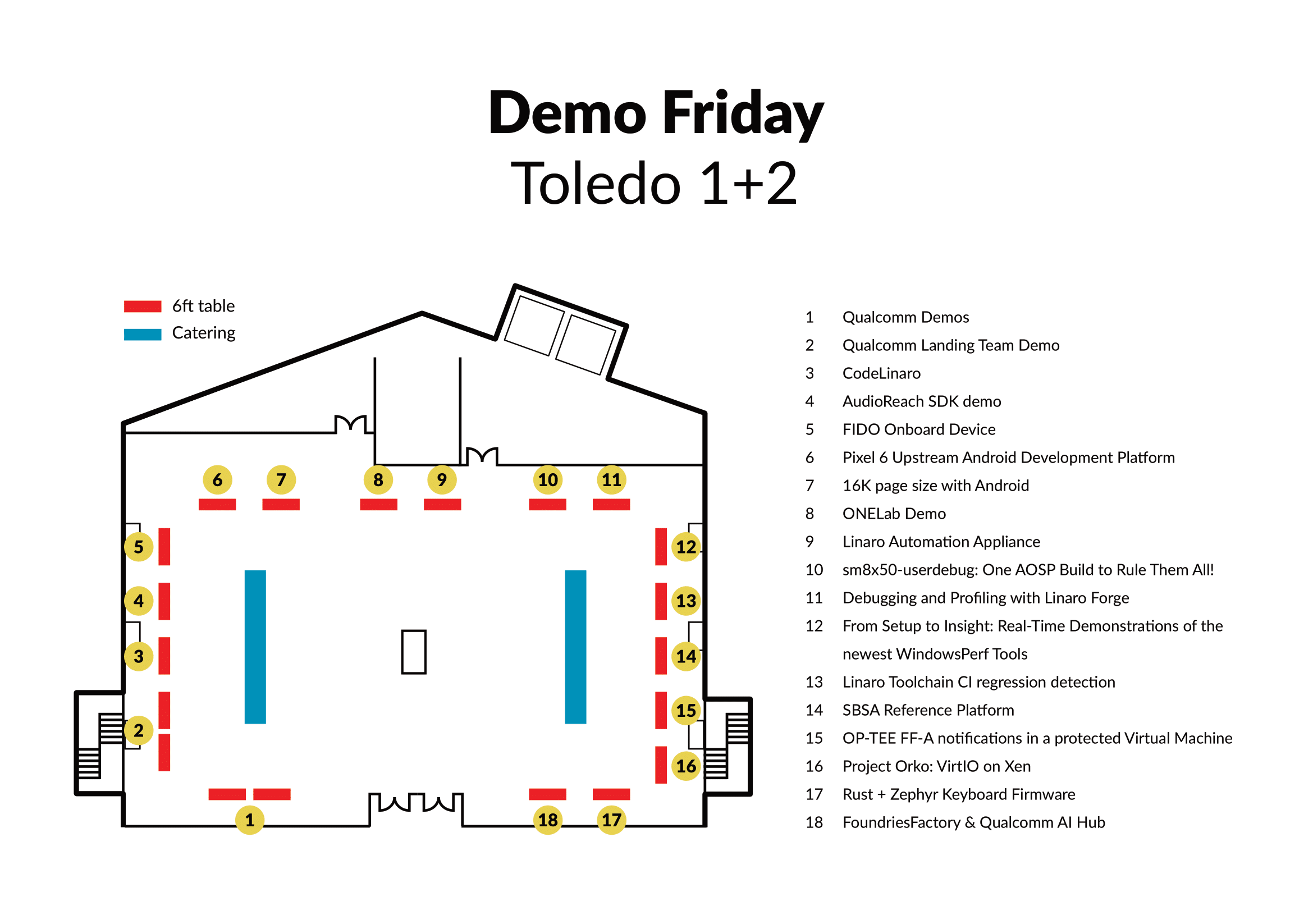
- Friday, 17 May 13:05 - 15:00
- Room: Demo Friday | Toledo
MAD24-209 Ask Arm Anything [MEMBERS / Arm PARTNERS ONLY, Must show badge when entering]
Session
- Wednesday, 15 May 11:10 - 12:10
- Room: Keynote | Zaragoza III+IV
[MEMBERS / Arm PARTNERS ONLY, Must show badge when entering]

SVP Software at Arm
MAD24-106 Many ways to learn Rust
Training
- Tuesday, 14 May 15:10 - 15:35
- Room: Session 3 | Tenerife II
There are lots of great reasons to learn Rust and there are lots of great resources available to help you learn Rust. This talk is focused on the second of these things: the tools that can help you learn Rust combined with practical suggestions on how you can use them effectively. Having discussed some of the available resources, we will look at a variety of different routes that could be taken to learn the language, and how each uses the resources. You can't leave such a short session knowing how to write Rust, but Daniel wants you to leave knowing how to learn Rust.

Tech Lead at Linaro
MAD24-212 Arm System Architecture and SystemReady Update
Session
- Wednesday, 15 May 12:20 - 12:45
- Room: Keynote | Zaragoza III+IV
This sessions provides a detailed update to the system architecture standards such as BSA, xBSA, and BBR that covers the hardware and firmware requirements necessary for the generic OSes to boot/install without modifications and for software standardization of hardware features specific for market segments. In addition SBMR update is provided that covers the server management standardization effort. This session will also provide an update on the SystemReady certification program.

Fellow at Arm
MAD24-103 Does System Ready IR "Just Work"?
Session
- Tuesday, 14 May 14:35 - 15:00
- Room: Session 2 | Tenerife I
In adding support for System Ready IR to Texas Instruments development boards, I will take a look at how effective the standard is at meeting its goal of software that 'just works'. In particular, I will cover - Firmware availability - Device Tree and its stability over kernel versions - Support in distributions for updating firmware via Capsule update - Firmware update robustness
Eng Manager at Texas Instruments
MAD24-105 Looking back on SystemReady IR
Session
- Tuesday, 14 May 15:10 - 15:35
- Room: Session 2 | Tenerife I
SystemReady is Arm's compliance program for ensuring compatibility between Arm A-Profile platforms and the operating system ecosystem. The SystemReady IR band is tailored to meet the needs of the embedded Linux market. It is based on UEFI and Devicetree, with a typical firmware stack comprising U-Boot, TF-A, OP-TEE and StMM. In this presentation we will look back on the SystemReady IR journey, since it was first announced in 2020, from IR 1.0 to the IR 2.1 latest version of the certification. We will contemplate the evolution of the specifications and the concerned components, such as U-Boot. We will also give some statistics on the past SystemReady IR certifications.

System Architect at Arm
MAD24-110 U-Boot for SystemReady IR - Status and struggles
Session
- Tuesday, 14 May 15:55 - 16:20
- Room: Session 2 | Tenerife I
U-Boot has been used to certify IoT platforms since its 2021.04 release. However, the certification is not always easy. On top of that the device functionality and security profile heavily depends on the available hardware options. Let's have a community talk briefly presenting the current state and future roadmap that would make certification easier.
Senior Tech Lead at Linaro
MAD24-306 Qualcomm and SystemReady IR, an overview of Qualcomm support in U-Boot (and what the future holds)
Session
- Thursday, 16 May 10:25 - 10:50
- Room: Session 1 | Las Palmas I
For the last year Linaro have been working on building a SystemReady UEFI solution for Qualcomm boards based on U-Boot. Caleb will explain what motivated this work, describe the current status and talk about some of the cool U-Boot features we can leverage on Qualcomm boards.
Engineer at Linaro
MAD24-318 What's Qualcomm upto in IoT??
Session
- Thursday, 16 May 12:10 - 12:35
- Room: Session 1 | Las Palmas I
The Internet of Things (IoT) market has undergone significant evolution since its inception, transforming the way businesses and individuals interact with technology. The evolution of IoT markets can be traced through several key phases of Emergence and Proliferation which led to Standardization and Interoperability and followed by Edge Computing, 5G connectivity with Low Power Device and Secure Devices. Qualcomm Introduced Robotics platforms (RB3 and RB5) earlier with Linaro 96 Boards to help address the open source IoT markets and Linaro has been helping with open source Software support for these platforms. This was followed up with RB1 and RB2 platforms which address the low and mid tier market segment. Now, Qualcomm is also launching RB3 and RB5 Gen 2 platforms. This session will focus on the journey of open source software solutions for Qualcomm RB platforms, explore the support for Linux kernel, U-Boot and discuss the current status of SystemReady-IR and explore future possibilities with RB platforms.
Senior Tech Lead at Linaro
MAD24-314 AudioReach Open Source Project
Session
- Thursday, 16 May 11:35 - 12:00
- Room: Session 1 | Las Palmas I
AudioReachTM is a comprehensive and complete end-to-end audio software solution that Qualcomm developed to support a broad range of audio and voice use cases across a diverse set of SoC’s and product devices (handset, compute, wearables, hearables, xr, automotive telematics / infotainment, etc). The AudioReach SDK contains the essential components to support a seamless development workflow from off-target to on-target and flexibility to customize and tailor the processing to the capabilities and constraints of the SoC and product device (multiple cores, peripheral devices, etc). Qualcomm would like to share this solution with the broader audio ecosystem as a community sponsored open source project and collaborate with the community to improve and evolve this solution over time. This presentation will introduce the AudioReach solution and objectives for the open source project.
Software Engineer at Qualcomm
MAD24-211 Boot time optimization project
Session
- Wednesday, 15 May 11:45 - 12:10
- Room: Session 2 | Tenerife I
Systems with industry standards like automotive have strong requirements to ensure the boot process is fast enough to put the system in a ready state. Others consider the boot time less important when the system is powered up but want a quick wake up from an hibernate state. The platform boot time optimization is usually platform specific and use case centric which implies a dedicated set of changes. Those will be deprecated with a new hardware having different drivers or a new software version which may introduce latencies in the boot time process. The boot time optimization project aims to put in place a continuous integration loop to monitor the boot timings and detect regressions over updates. In addition, from an engineering point of view, it identifies a set of changes to be done in the different steps of the boot chain, from the firmware to the userspace. This presentation will describe the project which is split into two parts. The first part will present the boot time continuous integration architecture. We will also discuss the boot timings information to be passed along the different components of the boot chain and how to standardize them in order to retrieve the information in the monitoring process. The second part will list a set of identified bottlenecks responsible for latencies in the boot process. We will propose a way to fix them up and discuss the solutions. It is also an opportunity to share our experience and point out other bottlenecks we may have missed.
Kernel Engineer & Power Specialist at Linaro
MAD24-208 Improving Delivery Process Performance for Software-Defined Products Helped by Data Analytics
Session
- Wednesday, 15 May 11:10 - 11:35
- Room: Session 2 | Tenerife I
Most of what we know today about applying delivery metrics today comes from software production environments where the organization has significant or full control of the product deployment. How do we apply such metrics in environments where your control of the deployment environment is limited or non-existent? What if it is not a software-only product but a software-defined one (including HW)? What if there is a supply chain involved you have to collaborate with in order to create the product actively? What if there are regulations involved? Is our approach to delivery metrics similar in all those cases or do we need to adapt them? What adaptations do we need to apply? This session, tailored for software engineers and data scientists, will delve into some of the lessons learned when applying delivery metrics and other key metrics to such environments, as well as some of the challenges we have faced. It will also describe the lessons learned from open source we are applying when implementing data analytics into production environments that have worked well. This talk aims to elucidate how analytics-driven assessments empower software engineering teams with insights, aiding in process and practice refinement, identifying bottlenecks, silos, waste, etc., and fostering continuous improvement with a noticeable impact on both, the overall organizational performance and the workforce well-being.

CEO at Bitergia

Consultant at Toscalix
MAD24-206 Linaro Automation Appliance preview
Session
- Wednesday, 15 May 10:35 - 11:00
- Room: Session 2 | Tenerife I
The Linaro Automation Appliance is a new solution developed by Linaro to accelerate device automation by providing a full featured appliance. In the test automation community, LAVA has become the de-facto standard for the software. On the hardware side, most of the automation labs are using customs solutions. The Linaro Automation Appliance (LAA) goal is to provide a full-featured appliance for automating Device Under Test (DUT) in LAVA. Thanks to the LAA, lab admins can add new DUT to their lab in a few minutes. In this talk we will present the Linaro Automation Appliance unique features along with it's links with the LAVA Managed Service.
Principal Tech Lead at Linaro
Engineer at Linaro
MAD24-327 Implementing an FF-A Secure Partition Manager in Rust
Session
- Thursday, 16 May 15:45 - 16:10
- Room: Session 2 | Tenerife I
The Arm Firmware Framework for Arm A-profile (FF-A) specification defines the software architecture of firmware components and their standardized communication protocol. The specification offers isolation of mutually mistrusting components using the architectural features of Arm's A-profile CPUs. It defines the Secure Partition Manager (SPM) component, which is responsible for the compartmentalization and the communication of the Secure Partitions. Rust is an ideal choice for security focused software due to its memory safe nature and performance characteristics. The language has started to gain traction due to adoption by major companies and regulators starting to advocate for memory safe languages. In this talk we'd like to present our FF-A Secure Partition Manager prototype implemented in Rust, and discuss the benefits and challenges of using Rust in a firmware project. The current implementation is able to run S-EL0 Secure Partitions (e.g. from the Trusted Services project). The SPM can run in S-EL1 or in S-EL2 if VHE is present. This is an experimental proof-of-concept project, published on TrustedFirmware.org (https://git.trustedfirmware.org/rust-spmc/rust-spmc/).
Staff Software Engineer at Arm
Senior Software Engineer at Arm
MAD24-323 Extending libcamera to provide a fully open camera SoftISP stack
Session
- Thursday, 16 May 14:20 - 14:45
- Room: Session 1 | Las Palmas I
A generic solution that takes V4L2 raw pixel data and converts to a format that can be used in Linux "cheese" on Hangout or Zoom. Developed in parallel on x86 and Arm a fully open ISP camera stack in libcamera means that common code, common bugfixes and more generic cross-architectures solutions are possible. libcamera SoftISP solves the problem of debayering and 3A for SoCs which don't support HardISP upstream but also benefits the community in the common approach it provides across SoCs. Engineers from libcamera, Linaro, Red Hat and the wider community collaborated on delivering a SoftISP which can be used on any V4L2 compatible device.
Engineer at Linaro
MAD24-321 SystemReady as the default option for BSPs - Findings from the last SystemReady IoT workshop
BoF
- Thursday, 16 May 13:45 - 14:10
- Room: Session 1 | Las Palmas I
In February, SystemReady's Advisory Committee organized a workshop focused on outlining an optimal reference stack for Rich IoT edge devices, fostering security and interoperability between platforms and operating systems. Participants from across the wide supply chain, including representatives from System Integrators, OSVs, ISVs, ODMs, OEMs, and SIPs, shared their perspectives on the guiding principles of an effective stack, the standards that uphold those principles, and the existing implementations. This BoF session aims to present the workshop's conclusions and facilitate an open dialogue regarding any identified gaps. Additionally, it seeks to brainstorm the most effective approaches to address these gaps in the short term.
Senior Tech Lead at Linaro
Director of Technology at Arm
Senior Principal Edge and IoT Architect at Red Hat
MAD24-217 Android BoF
BoF
- Wednesday, 15 May 14:55 - 15:20
- Room: Session 3 | Tenerife II
Birds of Feather session to talk about all things Android.
Tech Lead, LCG at Linaro

Senior Engineer at Linaro
Engineer at Linaro
MAD24-320 Qualcomm and Upstream Kernel BoF
BoF
- Thursday, 16 May 13:45 - 14:10
- Room: Session 2 | Tenerife I
BoF aims at providing platform to discuss state of Qualcomm SoCs and Platforms support in Mainline Linux Kernel. Focusing mainly on. -> Where we are, Current Status of Qualcomm drivers. -> Ongoing efforts on new Drivers/Frameworks. -> Pending problems to solve and plan of attack. Along with open discussion around multiple ongoing efforts around Qualcomm Linux Eco system. This will be co-presented by some of Qualcomm Landing Team Engineers.
Kernel Engineer at Linaro

Senior Software Engineer at Linaro
MAD24-109 10 years with OP-TEE
BoF
- Tuesday, 14 May 15:55 - 16:55
- Room: Keynote | Zaragoza III+IV
In June 2024 it's 10 years since OP-TEE was published as an open source project. OP-TEE has been a significant project for Linaro and it has been used as a reference TEE implementation at Arm. Also in addition to that it's used by lots of organizations, companies and vendors for all sorts for purposes, like products, research, development etc. We'd like to run a panel discussion with the people who have been involved in the project where we discuss the history, the things that went good, what has been challenging and where we see OP-TEE go in the future.

Distinguished Engineer at Linaro

Senior Software Engineer at Linaro

Senior Engineer at Linaro

SW engineer at ST
MAD24-226 LLVM Glibc project
BoF
- Wednesday, 15 May 16:20 - 16:45
- Room: Session 1 | Las Palmas I
The glibc is a known missing link for a distribution that aims to use clang as the default compiler. And since it is developed along with other GNU toolchain projects, it relies on various gcc extensions which are not readily available on clang. This talk walks through the required changes, the compiler's subtle differences, and some corner cases, to allow glibc to build with clang and its tools. Besides the library itself, glibc also contains an extensive test suite that tests not only its own provided API but also requires extra compiler support. This also requires additional changes to assert that the clang generates the correct code.
Toolchain Software Engineer at Linaro

Senior Software Engineer at Linaro
MAD24-218 Introducing the next generation of Arm Compiler
Session
- Wednesday, 15 May 14:20 - 14:45
- Room: Session 1 | Las Palmas I
In this session, Arm would like to provide a technical introduction to the next generation of our flagship commercial toolchain, Arm Compiler. This new toolchain represents a shift in strategy towards open source components, and is very closely related to the open source [LLVM Embedded Toolchain for Arm](https://github.com/ARM-software/LLVM-embedded-toolchain-for-Arm). Leveraging open source components allows us easier collaboration with the community, as well as making it easier to offer upstream features such as support for security sanitizers. This toolchain aims to meet the changing needs of the internet-of-things and Automotive sectors, where use of POSIX RTOS and C++ is getting popular due its greater portability and software reuse. This presents a challenge - and opportunity - to toolchains such as Arm Compiler, to provide support for higher level language constructs, especially when used in Functional Safety.

Compiler Technology Manager at Arm
MAD24-216 What Can Static Analysis Do For You (Smatch)
Session
- Wednesday, 15 May 13:45 - 14:10
- Room: Session 1 | Las Palmas I
This talk will cover the current state of static analysis in the kernel: the successes and challenges. I am the author of Smatch so the talk will have a pro-Smatch bias, however it's not always the best tool. We will go through some example bugs and see how they could have been prevented using static analysis.
Software Engineer at Linaro
MAD24-307 *Arm64 Linux kernel Architectural Updates*
Session
- Thursday, 16 May 10:25 - 10:50
- Room: Session 2 | Tenerife I
The Arm64 Linux Kernel is constantly evolving to align with the disruptive Arm architecture enablement story, spanning across 3 spheres : performance, compute and security. At Arm, we drive this kernel enablement story to facilitate our architecture adoption. The shared ownership helps us to sustain the value of upstream contribution in the bigger Linux Kernel community. This talk walks us through the Arm architectural upstream story comprising deltas from 2021/2022 extensions (v8.8,v8.9 arch), CCA kernel highlights, advanced Arm arch features for 2023+ extensions, mainly from kernel perspective, touching on Distros wherever applicable. The session also provides a forward looking deliberation for investigation areas to be explored in the Kernel space.
Software Product Manager at Arm
MAD24-309 Enabling the FF-A software standard for KVM Virtual Machines
Session
- Thursday, 16 May 11:00 - 11:25
- Room: Session 2 | Tenerife I
The FF-A firmware standard (https://developer.arm.com/architectures/Firmware%20Framework%20for%20A-Profile) defines a software ABI that normal and secure world software (as defined in the ARM v8/v9 aarch64 architecture) components can leverage in order to communicate through memory sharing, messages (synchronous and asynchronous) and notifications. This talk provides insight into the ongoing work carried out to enable FF-A deployment on current systems with a specific focus on KVM virtual machines enablement (ie communication between normal world virtual machines and secure world aka TrustZone).
Principal software engineer at Linaro
MAD24-308 Enhancements in WindowsPerf
Session
- Thursday, 16 May 11:00 - 11:25
- Room: Session 3 | Tenerife II
In this presentation, we will delve into the significant advancements made in WindowsPerf. Our journey of improvement has been marked by enhancements in several key areas, including counting, sampling, and the timeline feature, which have all seen substantial upgrades. One of the major changes is the introduction of a new GUI, a hybrid of the Visual Studio extension and WPA plugin, both sub-projects of WindowsPerf. This combination has resulted in a more intuitive and user-friendly interface, making WindowsPerf more accessible to users. Furthermore, we have made considerable strides in improving the stability of the Kernel Driver. This enhancement has significantly reduced system crashes and improved overall performance. In our quest to provide more comprehensive performance metrics, we have added support for Neoverse PMU events and metrics. This addition allows users to gain deeper insights into system performance and make more informed decisions. Lastly, we have introduced disassembly for the annotate feature, providing users with a more detailed view of their code and its performance.
Senior Software Engineer at Linaro

Principal Engineer at Arm

Software Engineer at Day Devs
MAD24-324 Trusted Firmware Project updates and 10 years of TF-A.
Session
- Thursday, 16 May 14:55 - 15:20
- Room: Session 2 | Tenerife I
Trustedfirmware.org open source community project is providing a collaborative platform for the security experts from the wider community to build scalable security. Over the years, the project has grown with multiple projects providing secure software implementation for Armv8-A, Armv9-A and Armv8-M. As we celebrate 10 years of the Trusted Firmware-A project, the session would cover recent significant project milestones, key project initiatives (LTSs, MISRA), new members and roadmaps.

Director, Software Technology Management at Arm
Director, Software Technology Management at Arm
MAD24-214 Modern CI solutions for Linux Kernel Testing
Session
- Wednesday, 15 May 12:20 - 12:45
- Room: Session 2 | Tenerife I
Today's landscape boasts a variety of CI/CD platforms, including GitHub, GitLab, CodeLinaro, and Jenkins. Recently, patches were submitted for enabling pipeline solutions into the Linux Kernel tree. Our aim is to enhance transparency in testing solutions, thereby maximising the value developers derive from the outcomes. In our presentation, we will explore several innovative approaches, particularly focusing on Linaro's open-source contributions like TuxMake and TuxRun. These tools facilitate building and testing the Linux kernel within GitLab pipelines and GitHub Actions. Furthermore, we will delve into advanced testing strategies that leverage cloud resources for build and test processes through TuxSuite. A significant portion of our discussion will be dedicated to Curated TuxSuite Plans that outline specific builds and tests for various subsystems, triggered by relevant patches to those subsystems. This approach not only streamlines the testing process but also ensures targeted and efficient testing aligned with subsystem changes.

Tech Lead at Linaro
MAD24-403 Optimising oneDAL and oneDNN for Arm CPUs to accelerate AI workloads
Session
- Friday, 17 May 10:20 - 10:45
- Room: Session 1 | Las Palmas I
We at Fujitsu aim to deliver a high-performance, energy-efficient Arm-based CPU for data centres named FUJITSU-MONAKA. To achieve this goal, Fujitsu is focusing on application performance, ease of use, and open-source software. This abstract investigates the optimisation of AI workloads utilising the oneDNN and oneDAL libraries to accelerate AI workloads on Arm CPUs. Successfully ported oneDAL on Arm, leveraging SVE and incorporating enhancements with open-source optimized compute kernels of OpenBLAS, resulting in notable performance gains across multiple AI algorithms. Fujitsu has also contributed implementation of batch-reduced GEMM-based JIT kernels for MatMul and Convolution primitives, as well as expanding JIT kernels to support multiple ISAs, enabling them over more CPUs such as A64FX and Graviton3E. We acknowledge the NEDO Project “Technology Development of the Next Generation Green Data Centre” for the “Green Innovation Fund Project/Construction of Next Generation Digital Infrastructure." NEDO is the “New Energy and Industrial Technology Development Organisation," a national research and development agency in Japan. This presentation is based on results obtained from a project, JPNP21029, subsidised by the New Energy and Industrial Technology Development Organisation (NEDO)

Software Engineering Manager at Fujitsu
MAD24-407 The path to mainline for NPU drivers
Session
- Friday, 17 May 10:55 - 11:20
- Room: Session 1 | Las Palmas I
The current situation regarding the Linux kernel and drivers for NPUs is similar to that of GPU drivers 5 years ago. Out-of-tree kernel drivers hinders companies' efforts to use the latest Linux kernels, and the ad-hoc closed source userspace stacks from each IP vendor is very costly in terms of integration and support. This session will explain a existing path for NPU drivers to be upstreamed to the Linux kernel, allowing companies to effortlessly and safely use the latest kernels in their products, and integrating the user-space drivers within the standard Linux ecosystem.

Open-source engineer at Independent contractor
MAD24-412 Accelerate your AI workloads on Windows on Snapdragon
Session
- Friday, 17 May 11:30 - 11:55
- Room: Session 1 | Las Palmas I
In this session, developers will delve into the world of AI powered by the Qualcomm Snapdragon X-Elite platform. Attendees will gain insights into leveraging cutting-edge AI capabilities for Windows applications. Highlights include: Understanding Snapdragon X-Elite Benefits: - Explore the unique AI features and optimizations offered by Snapdragon X-Elite. - Learn how it accelerates AI workloads, enhances inference performance, and optimizes power efficiency. Hands-On Deployment of Large Language Models: - Get hands-on experience deploying large language models like Llama2 directly on-device. - Get a deep dive on the Qualcomm AI SDKs to deploy models efficiently. Join us to unlock the potential of AI on ARM-powered Windows devices and elevate your app experiences!

Senior Product Manager at Qualcomm
MAD24-315 Rethinking the kernel system call entry
Session
- Thursday, 16 May 11:35 - 12:00
- Room: Session 2 | Tenerife I
The kernel currently contains two different ways of generating system call tables across architectures, with bits of it abstracted by rather complicated macros that are universally hated and that that occasionally run into dangerous corner cases when they are wrong. Arnd is working on a rewrite of this code to end up with a version using generated code to make this consistent across all architectures. The resulting infrastructure will allow correct argument sanitation for compat syscalls for architectures that support 32-bit compat binaries, At the same time describing system calls enough to have the user space side generated from the same description, which can be used by things like the C library, debugger or tracing in userspace. Adding a new system call should become a matter of editing a single file, and it will be easier to add support for additional ABIs such as 128-bit pointer userspace coexisting with the current 32-bit and 64-bit binaries.
Kernel maintainer at Linaro
MAD24-316 MAD24-318 Why TLBI matters on ARM server: scalability issues we found and solutions
Session
- Thursday, 16 May 12:10 - 12:35
- Room: Session 2 | Tenerife I
TLBI is the TLB invalidation which is needed for updating mappings and attributes of the page table, on ARM the TLBI will broadcast to every CPU core in the inner shareable domain, and we found that TLBI affects the scalability a lot on some workload (such as virtual machine) on ARM64 server with many CPU cores. In this presentation, we introduce some scalability mitigations for TLBI such as TLBI by range, batched TLBI in the Linux mainline kernel. Then present the scalability issue we encountered on our ARM server when running VMs, we limit the TLBI in VM cpu context domain then we got about 50% performance boost on a 96 core ARM server.
Engineer at Huawei
OS kernel Architect at Huawei
MAD24-223 State of LLVM Flang Development
Session
- Wednesday, 15 May 15:45 - 16:10
- Room: Session 1 | Las Palmas I
LLVM’s Fortran compiler, Flang, is under active development and advancing at a rapid pace, getting closer to being considered production ready. In this presentation you will learn about the current status of Flang, the features it supports and how its performance compares against that of other Fortran compilers. In particular, improvements and bug fixes driven by Fujitsu and GFortran test suites, which contain years of code derived from real world usage and that now, for the most part, work with Flang. Other highlights are full support for polymorphism and OpenMP 1.1 and partial support for procedure pointers, C-interoperability, OpenACC and later versions of OpenMP.

Toolchain Engineer at Linaro

Senior Software Engineer at Linaro
MAD24-305 Boost your workload and platform performance on Windows on Arm with WindowsPerf
Session
- Thursday, 16 May 10:25 - 10:50
- Room: Session 3 | Tenerife II
Learn how to use WindowsPerf and Arm telemetry solutions to analyse performance and optimise your code. You will also learn how to use WindowsPerf Visual Studio extension and WPA-plugin for easier hotspot analysis and identification of system performance bottlenecks during code execution on Windows on Arm. Presentation will include live demos with commentary. Demos will include synthetic and real workloads.

Principal Engineer at Arm

Principal System Architect at Arm
MAD24-312 Optimising for Windows on Arm: A Deep Dive into WindowsPerf’s Newest GUI Tools
Session
- Thursday, 16 May 11:35 - 12:00
- Room: Session 3 | Tenerife II
The WindowsPerf Visual Studio Extension enriches the developer experience by allowing direct execution of performance sampling and analysis within the IDE. This enables valuable insights and annotations of performance hotspots in source code. In addition, the WPA Plugin amplifies Windows Performance Analyzer's functionality to process and visualise WindowsPerf data, facilitating a comprehensive analysis. Our presentation, tailored for developers and performance analysts, will feature live demonstrations to illustrate the seamless integration of these tools into the development workflow. Attendees will learn how to effectively utilise these tools to identify and remedy performance issues swiftly. As we continue to evolve these tools, we invite the community to join us in refining and expanding their capabilities through our open-source projects.

Software Engineer at Day Devs
MAD24-326 Kria Dynamic Board-ID & Device Tree Selection
Session
- Thursday, 16 May 15:45 - 16:10
- Room: Session 1 | Las Palmas I
Kria is a system-on-module (SOM) platform that enables multiple application specific I/O and peripherals through a set of application carrier cards (CC). To support multiple CC with a common boot firmware and software the Kria platform has implemented a dynamic board-ID, peripheral enablement, and device tree handling to support multiple HW configurations with a shared solution stack. This session will review the problems solved with this solution, detailed technical architecture, example implementations, and potential future work.
Fellow - Systems Architecture at AMD
Developer at AMD
MAD24-207 Align the kernel upstream approach with the userspace in power management
Session
- Wednesday, 15 May 11:10 - 11:35
- Room: Session 3 | Tenerife II
The awareness of the cost resulting from the Android kernel fragmentation led to a convergence to a Linux kernel upstream support based on a Generic Kernel Interface (GKI). The effort for supporting upstream SoCs is unfortunately slowed down when the kernel and the userspace have to be aligned. The interfaces presented by the custom kernels are not standardized. Consequently, the userpsace which is relying on those interfaces can no longer interact with the kernel when the upstream support is brought up and the overall power management can not be enabled in Android. Linaro has developed a set of userspace components designed to be generic in order to provide basic power management support with the Linux kernel upstream enablement. On the other side, efforts are made in the background to bring standardized power management interfaces from the kernel and have the generic userspace components to take advantage of them. This presentation will give the architecture and the approach of the different userspace components. It will explain how to use them for an upstream platform enablement and will discuss the future of those for a more complete solution.
Kernel Engineer & Power Specialist at Linaro
MAD24-215 Cuttlefish + Generic Android Bootloaders
Session
- Wednesday, 15 May 13:45 - 14:10
- Room: Session 3 | Tenerife II
Cuttlefish is a virtual device platform meant for Android development and supported by Google since 2017. I'll cover the state of the platform and what the team is working on this year. Amongst these projects is a generic Android Boot solution (ABL) we've been developing this past year which leverages EFI. I'll cover that in some more detail and discuss how we'd like to take it forward.
Software Engineer at Google
MAD24-204 Pixel 6 and Tensor G1 SoC upstreaming status and plans
Session
- Wednesday, 15 May 10:35 - 11:00
- Room: Session 3 | Tenerife II
During this talk we will explore Google's efforts in collaboration with the Linaro Google landing team to create an upstream Android development platform with the Pixel 6 device and Tensor G1 SoC. We will explore * The current status of Tensor G1 SoC and Pixel 6 upstreaming work. * Tentative roadmap of features landing upstream * How we keep the downstream Pixel drivers evolving with upstream kernel APIs and the benefits this brings * Future plans
Tech Lead Google Landing Team at Linaro
MAD24-220 LCG Lightning Talks
Session
- Wednesday, 15 May 14:20 - 14:45
- Room: Session 3 | Tenerife II
A series of short talks about various topics of work that Linaro Consumer Group have been working on.
Tech Lead, LCG at Linaro

Senior Engineer at Linaro
Engineer at Linaro
MAD24-213 devboardsforandroid: An update
Session
- Wednesday, 15 May 12:20 - 12:45
- Room: Session 3 | Tenerife II
devboardsforandroid.linaro.org was started as a collaborative space to collect devboards aimed to be enabled with AOSP. This session provides an update since, and takes us through the SM8550 enabled as a device using this space.
Tech Lead, LCG at Linaro

Senior Engineer at Linaro
MAD24-304 Leveraging Atomic Upgrades with OSTree for Automotive
Session
- Thursday, 16 May 10:25 - 10:50
- Room: Keynote | Zaragoza III+IV
In the rapidly evolving automotive industry, software updates have become a critical aspect of vehicle maintenance and functionality enhancement. However, updating software in vehicles presents unique challenges, including ensuring reliability, security, and minimizing downtime. In this proposal, we advocate for the adoption of atomic upgrades utilizing OSTree technology in automotive systems. We will discuss the benefits, challenges, and implementation strategies of using OSTree for automotive software updates. Our talk will provide valuable insights into leveraging atomic upgrades to streamline the update process, enhance system reliability, and improve overall user experience in automotive software management. Introduction: As vehicles become increasingly connected and reliant on software-driven features, the need for efficient and reliable software update mechanisms becomes paramount. Traditional update methods often involve complex processes, significant downtime, and potential risks to system integrity. Atomic upgrades offer a promising solution by ensuring system consistency and reliability during the update process. OSTree, a versioned file system designed for immutable deployment of filesystem trees, provides a robust foundation for implementing atomic upgrades in automotive systems. This proposal aims to explore the integration of OSTree-based atomic upgrades in automotive software management. Key Points to be Covered: 1. Overview of Atomic Upgrades: We will provide a comprehensive overview of atomic upgrades, explaining the concept and highlighting its advantages over traditional update mechanisms. This section will cover key principles such as atomicity, transactionality, and rollback capabilities. 2. Introduction to OSTree: We will delve into the features and architecture of OSTree, emphasizing its suitability for automotive software deployments. Topics covered will include versioning, deduplication, and content-addressable storage. 3. Benefits of OSTree for Automotive: We will discuss the specific advantages of leveraging OSTree for automotive software updates. This will include improved reliability, reduced downtime, enhanced security, and simplified rollback procedures. 4. Challenges and Considerations: We will address the challenges and considerations associated with implementing OSTree-based atomic upgrades in automotive environments. Topics such as bandwidth constraints, storage requirements, and integration with existing systems will be explored. 5. Implementation Strategies: We will provide practical guidance on implementing OSTree-based atomic upgrades in automotive systems. This will include deployment considerations, tooling support, and best practices for ensuring a smooth transition to the new update mechanism. 6. Bootloader support: rpm-ostree, ostree, etc. has focused on UEFI-like platforms for compatibility, learn how you can run OSTree on UEFI-like platforms and alternate platforms 7. Introduction to composefs: Learn more about composefs, the latest and greatest immutable filesystem/ Conclusion: In conclusion, this talk will highlight the significant advantages of adopting OSTree-based atomic upgrades in automotive software management. By leveraging OSTree, automotive companies can enhance system reliability, streamline the update process, and improve overall user experience. We believe that this presentation will provide valuable insights for automotive developers, engineers, and decision-makers looking to optimize their software update strategies.
Principal Software Engineer at Red Hat
MAD24-310 Using logical performance and power domains to achieve resource abstraction over SCMI
Session
- Thursday, 16 May 11:00 - 11:25
- Room: Keynote | Zaragoza III+IV
Traditionally, the performance domains have been used only for CPU devices however there is no reason why it can't be used for non-cpu devices(i.e. peripherals). We aim to abstract peripheral resources such as clocks, regulators, interconnect, phy etc. using performance and power domains. In this approach, we define logical performance and power domains for the peripheral devices instead of dealing with clocks,regulator, interconnect etc. individually. We abstract resources in firmware and use SCMI power and perf protocols to to request/configure peripherals resources. This minimizes the traffic between the agent and platform thus improves boot KPIs. We will discuss upstreaming efforts etc. to achieve this.
Senior Staff Engineer at Qualcomm
MAD24-313 DENSO’s Approach for Mixed Critical Systems in SDV
Session
- Thursday, 16 May 11:35 - 12:00
- Room: Keynote | Zaragoza III+IV
In the automotive industry, there is an initiative to realize a new type of vehicle called Software Defined Vehicle (SDV), in which vehicle functionality and value are provided by software without relying on specific hardware.In SDV, software development technologies that seamlessly integrate cloud and embedded environments are required, and these technologies include diverse areas such as system modeling, mixed criticality, microservices, DevOps, and so on. In this session, we will explain the need for deterministic guarantees of behavior of Mixed Criticality Systems as a key issue in SDV, and introduce DENSO's approach to solving this issue and our activities in open consortium.

Technical Manager at DENSO AUTOMOTIVE
MAD24-319 Arm Reference Design-1AE - an Automotive solution
Session
- Thursday, 16 May 12:10 - 12:35
- Room: Keynote | Zaragoza III+IV
Following the release of the latest Arm Automotive Enhanced (AE) processors and IP, this session will review the architecture and software features of the FVP and software package delivered with the Automotive Reference Design-1 (RD-1 AE). This Reference Design integrates a high-performance compute subsystem built with the new Neoverse V3AE cores, and a multi-cluster Cortex-R82AE based Safety Island.

Senior Software Technology Manager at Arm
Software Architect at Arm
MAD24-317 Thinking the new intelligent operating systems for AI CAR
Session
- Thursday, 16 May 12:10 - 12:35
- Room: Session 3 | Tenerife II
The LLM has change the world, including the intelligent Vehicle system, it will not only affect the HMI mode, but also require to redefinition of the paradigm of human vehicle interaction, intelligent cockpitentertainment system, L3+ intelligent driving, and llm based AI Native agent So we need to think about how to build new intelligent OS for the new challenge, incluing Safety, AI Native, Edge Computing, Security, virtualization and more....
Chief Technical Expert at Huawei
MAD24-406 Orko where are we now - lessons from enabling VirtIO media devices
Session
- Friday, 17 May 10:20 - 10:45
- Room: Keynote | Zaragoza III+IV
Project Orko is a Linaro project that has been working on enabling VirtIO for complex edge devices across multiple hypervisors. In the last year we've been looking at enabling multi-media devices including sound and graphics. In this talk we shall look at some of the challenges we have encountered and the extra demands multi-media devices make of the VirtIO stack. We shall go into details about how the Friday demo was put together and what is still left to do and in what part VirtIO can play in glueing together complex edge systems.
Virtualisation and Emulation Tech Lead at Linaro
MAD24-408 Accelerator: UADK’s usage and development
Session
- Friday, 17 May 10:55 - 11:20
- Room: Keynote | Zaragoza III+IV
UACCE(Unified/User-space-access-intended Accelerator Framework) was upstream to Linux kernel version 5.7, and it targets to provide Shared Virtual Addressing (SVA) between accelerators and processes. So accelerator can access any data structure of the main CPU. It is jointly developed by Huawei and Linaro. Some open source projects have joint or are in the process of joining the UACCE, such as UADK(User Space Accelerator Development Kit), DPDK(Data Plane Development Kit), SPDK(Storage Performance Development Kit) and so on. We will share the current development status, the usage cases, the performance, and the future evolution of UACCE.
Software Engineer at Linaro
MAD24-411 Gunyah Accelerator for Qemu
Session
- Friday, 17 May 11:30 - 11:55
- Room: Keynote | Zaragoza III+IV
Gunyah is a high performance and scalable Type-1 hypervisor built for demanding battery-powered, real-time, safety critical systems and currently supports ARM64 architecture. A Linux driver for it is being developed taking active inputs from kernel maintainers and community. It will allow applications such as Qemu to interact with the hypervisor for VM management. The Linux driver is expected to be merged upstream very soon this year. Support for gunyah hypervisor in Qemu is also being developed concurrently with couple of versions already published. In this session, we intend to briefly cover Gunyah hypervisor overview, proposed features of its Linux driver and finally the proposed changes to Qemu for supporting Gunyah. We discuss the proposed changes to manage both confidential guests and non-confidential (aka unprotected) guests.
Principal Engineer at Qualcomm
MAD24-417 QQVP: Qualcomm's SystemC and Qemu modelling solution
Session
- Friday, 17 May 12:05 - 12:30
- Room: Keynote | Zaragoza III+IV
In today’s rapidly evolving tech landscape, developers face the challenge of running software for hardware which may not be available to them yet. Enter QQVP, Qualcomm’s QEMU based virtual platform solution which combines various models from several simulation frameworks together by means of SystemC. While QEMU offers a self-contained solution, QQVP takes it a step further. By allowing interoperability with external models, QQVP empowers developers to glue together legacy models, FPGA models, SystemC models, QEMU models, while communication is handled by SystemC Transaction Level Modelling. Join us as Antonio Caggiano and Mark Burton, seasoned expert from Qualcomm, unveil the inner working and capabilities of QQVP.

Staff Engineer at Qualcomm
at Qualcomm
MAD24-416 A journey to Git for Windows on AArch64, GNU Toolchain, GitHub CI, and Community Contributions
Session
- Friday, 17 May 12:05 - 12:30
- Room: Session 1 | Las Palmas I
This conference talk presents Git for Windows' journey, its evolution, and ongoing development. It discusses how CI practices enhance GNU toolchain contributions. It also shares insights from collaborating with Linaro on preparing patch series and gaining expertise in GNU toolchain contributions. It talks about introducing a new GCC target and facing community reviews as a new contributor. It looks at rebuilding Cygwin and MSYS2 toolchain from scratch and promoting Linux cross-compilation and MSYS2 toolchain repositories for community involvement.

Software Engineer at Microsoft

Senior Software Engineer at Microsoft
MAD24-420 Open source support for Arm's Mali-C55 ISP
Session
- Friday, 17 May 12:40 - 13:05
- Room: Session 1 | Las Palmas I
Arm's Mali-C55 ISP has started hitting silicon, and for the past year work has been underway to implement support for the hardware entirely through open source software. In this session we'll outline the work that's been done so far, covering the Linux kernel driver and the new pipeline handler within libcamera that combine to allow basic image capture through any application using the library. We'll also talk about the in-progress work to implement the delivery and consumption of parameters and statistics between the kernel driver and userspace along with an overview of the implementation of some of the most common image enhancement algorithms, such as Auto-Exposure and Auto-White Balance. Finally we'll cover our plans for future development and explain how you can use our work to integrate the ISP in your own software stacks and even enhance support by implementing custom image processing algorithms.
Software Engineer at Ideas on Board
Camera Specialist at Ideas on Board
MAD24-409 How to stay sane: Long Term Support, Government Mandates and Open Source
Session
- Friday, 17 May 10:55 - 11:20
- Room: Session 3 | Tenerife II
Long Term Support (LTS) for Open Source Software generally means that the community or a company is willing to support a particular version of software with fixes over an extend period of time. The idea is to not bring in new features only fixes to maximize compatibility. Great!?! Now what about what seem to be an increasing set of government rules/laws that mandate that the latest fixes make their way out to devices? Does a strategy based on LTS continue to work? We’ll consider what are the challenges to maintaining an LTS. What's in the best interest of maintainers? What's in the best interests software suppliers? We’ll look at the benefits to using an LTS. We’ll examine some of the situations where the strategy fails. How can you meet your computing needs by taking advantage of LTS software yet avoiding pitfalls that can come with it? Or how can you have a strategy that avoids LTS?
Director at Linaro
MAD24-404 Deploying and managing Confidential Virtual Machines on Arm platforms
Session
- Friday, 17 May 10:20 - 10:45
- Room: Session 2 | Tenerife I
Building on top of the work Arm has been doing with the community to enable the Arm Confidential Compute Architecture (CCA) on open-source projects, Linaro is contributing to make an open-source reference implementation of the whole CCA software stack by enabling support in QEMU, both as a Realm Management Extension (RME) emulation platform and a Virtual Machine Monitor (VMM) for Realms, Kata containers and Confidential Containers (CoCo) projects. We are also working on the important aspect of attestation verification of the confidential computing workloads. This talk describes the latest development made by the Linaro team and the community around this multitude of open-source projects to provide a complete software stack capable of deploying and managing confidential workloads on Arm platforms.

Principal Engineer at Linaro
Tech Lead at Linaro
Kernel Engineer at Linaro
Principal Engineer at Linaro
MAD24-410 Arm Confidential Compute Architecture open-source enablement update
Session
- Friday, 17 May 10:55 - 11:20
- Room: Session 2 | Tenerife I
The Arm Confidential Compute Architecture (Arm CCA) builds on top of the Armv9-A Realm Management Extension (RME) by providing a reference security architecture and open-source implementation of hypervisor-based confidential computing. This talk describes the latest open-source project developments (Trusted Firmware, Linux, KVM, EDK2) to enable Arm CCA, including current status, upcoming features and what to expect next.
Fellow at Arm
MAD24-414 SBSA Reference Platform in QEMU - status update
Session
- Friday, 17 May 11:30 - 11:55
- Room: Session 2 | Tenerife I
Many things happened around SBSA Reference Platform in QEMU during last years. From virtual hardware changes to firmware updates. In this talk I want to share machine's current status, what was changed and tested. How close we are to SBSA/SystemReady SR compliance. Also some bits of future plans.

Senior Software Engineer at Red Hat

Principal Engineer at Qualcomm
MAD24-421 The Status of Lustre on Arm64
Session
- Friday, 17 May 12:40 - 13:05
- Room: Session 2 | Tenerife I
In this session, we will report the latest status of Arm Lustre, such as what work we are doing on improving Arm Lustre support, Arm Lustre support status what OSes are supported and maintained and tested in our External Arm Lustre CI, and also the status of Arm Lustre adoption in production environment and so on.

Engineer at Linaro
MAD24-418 Software Pipelining Support for AArch64 in LLVM
Session
- Friday, 17 May 12:05 - 12:30
- Room: Session 2 | Tenerife I
Software Pipelining is a loop optimization technique that schedules instructions across iterations to increase instruction-level parallelism. We have been working on MachinePipeliner pass, an implementation of Software Pipelining in LLVM. We have already completed basic support for AArch64. In Neoverse V1, we observed that Software Pipelining improves performance for several cases where instructions within the target loop have long dependency chains. The results suggest that Software Pipelining is effective for such loops, even in modern OoO processors. Some of our patches have been merged and Software Pipelining for AArch64 is already available in the main branch. However, these patches are not the only end of our goal. We think of that there is various room for improvement in MachinePipeliner. For example, we must provide user interfaces to apply Software Pipelining like pragma. We will continue to contribute MachinePipeliner. This session will provide the details of our development and performance improvement
Software Engineer at Fujitsu
Software Engineering Manager at Fujitsu Limited
MAD24-405 A GDB to support debugging High Performance Computing (HPC) Applications: Upstreaming
Session
- Friday, 17 May 10:20 - 10:45
- Room: Session 3 | Tenerife II
Debugging High Performance Computing (HPC) codes presents several challenges. For example: multiple gigabytes of debug information, tens of thousands of processes and multiple third-party compilers with varying interpretations of DWARF. Forge GDB includes specialisation to handle these scenarios. Historically, these specialisations were provided through a 400+ out-of-tree patch set. However, this patch set was costing months of time per year to maintain. This factor forced a shift in approach from maintaining downstream changes to upstreaming. This shift towards upstreaming enabled further reductions in patchset size, reduction in maintenance cost from months to weeks, and made the HPC specialisations available to a wider audience out-of-the-box.

Software Developer at Linaro
MAD24-413 So, you want to encrypt?
Session
- Friday, 17 May 11:30 - 11:55
- Room: Session 3 | Tenerife II
A commonly heard adage in security is "never design your own cryptography". Related to this is advice that you also shouldn't design your own protocol. In this talk we will start with what seems to be a simple requirement for cryptography, and go through developing a protocol around this, seeing the pitfalls and traps that await us. We will end with an open standard that supports this requirement, hopefully with a better understanding of the complexity and intricacies behind it.

Senior Engineer at Linaro
MAD24-415 Enabling mobile trust thanks to DPE/DICE in Android
Session
- Friday, 17 May 12:05 - 12:30
- Room: Session 3 | Tenerife II
The DICE attestation scheme is used in Android pVMs to establish trust towards the device. The DPE spec enhances the original idea to move all the related computation into a secure enclave to enforce HW protection. ARM's RSE IP has the required security attributes to host a DPE service. The DPE service (hosted by RSE) was developed within the firmware team and it has been integrated with the wider firmware space (TF-A, U-Boot) and with the software stack of Android pVMs. The goal is to give an overview of the work done and promote the DPE-based attestation solution.
Principal Software Engineer at Arm
MAD24-419 OP-TEE device drivers frameworks
Session
- Friday, 17 May 12:40 - 13:05
- Room: Session 3 | Tenerife II
OP-TEE OS offers an almost full software implementation of the GP TEE APIs and other services exposed to trusted applications and to non-secure OSes. However, OP-TEE OS also offers several frameworks to ease integration of device drivers for platform resources from system resources (clocks, interrupts, …) to cryptographic hardware assistance and peripherals. These drivers can rely on device-tree or not to manage their configuration and dependencies. Several such frameworks were added in recent OP-TEE releases. This session proposes a tour in the device driver frameworks available in OP-TEE and is an opportunity to discuss with the attendance on possible evolutions.

SW engineer at ST
MAD24-311 TianoCore community update
Session
- Thursday, 16 May 11:00 - 11:25
- Room: Session 1 | Las Palmas I
TianoCore is the project that maintains the edk2 project, the UEFI reference implementation, as well as other related projects - like edk2-platforms. It's been quite a few years since we talked about these at Connect, so here are some updates on: changes since before the plague, upcoming changes to processes, upcoming changes to codebases, new features.

Principal Engineer at Qualcomm
MAD24-221 MSVC ARM64 optimization in Visual Studio
Session
- Wednesday, 15 May 14:55 - 15:20
- Room: Keynote | Zaragoza III+IV
Over the past year a team of ARM software engineers has been collaborating with MSVC compiler team focusing on improving compiler backend optimization on ARM64 platform. This presentation will highlight improvements that has been added to Visual Studio 2022 in version 17.6-17.9. We will also discuss the current and future plant to support ARM technology in toolchains.
Staff Software Engineer at Arm
MAD24-325 Simple, Yocto, Secure Boot: Using new systemd features to pick all three!
Session
- Thursday, 16 May 14:55 - 15:20
- Room: Session 1 | Las Palmas I
Recent systemd releases have introduced several new features to improve secure boot and add support for use cases around “Image-Based Linux”. Yet, adoption of these features in the embedded Linux world is slow. This talk tours a couple of these features and discusses their potential to simplify common embedded or edge computing use cases. We will explore recently added secure boot components (unified kernel images, systemd-boot, systemd’s initramfs services, systemd-repart) in a Yocto environment. Some of these new components were developed for non-embedded use cases, and we will need to deploy them in slightly different scenarios. We will discuss the remaining challenges and unsolved parts. The result is a sketch towards a turn-key solution to secure user-space for embedded Linux devices – and a TODO list of what is left to be done.

Engineer at Linaro
MAD24-205 Overview of Linaro Toolchain CI configurations
Session
- Wednesday, 15 May 10:35 - 11:35
- Room: Session 1 | Las Palmas I
In this session the Linaro Toolchain team will present the various configurations we are tracking in our CI and the insights we get. CI configurations include building Linux kernel, running GNU and LLVM testsuites, building Android/AOSP, and benchmarking SPEC CPU2017. It shows how these very different usages rely on the same core infrastructure to track multiple git repositories, bisect problems down to a single commit, and report regressions to upstream developers.
Toolchain Tech Lead at Linaro
MAD24-210 Advanced features of Linaro Toolchain CI
Session
- Wednesday, 15 May 11:45 - 12:45
- Room: Session 1 | Las Palmas I
The Linaro Toolchain CI has particular features not commonly available in other CIs. They enable automatically running the full binutils, GCC, GDB, and glibc testsuites on new upstream commits and quickly detect regressions, bisect them down to a single commit, even in the presence of flaky tests. Also, multiple components can be tested at the same time, and even emulators such as QEMU can be part of the test regimen. In benchmarking mode, it enables us to detect effects of new compiler optimizations on the standard C and math libraries. In this presentation, you will learn about these features and see examples of them in action. We recently added pre-commit testing. We’ll see the impact of this extension on the community. Finally, we’ll share some feedback from the community, illustrating how this is perceived as a major step forward, once we have managed to avoid false alarms caused by flaky tests.
Software Engineer at Linaro
Toolchain engineer at Arm

Software Engineer at Linaro
MAD24-219 Visual comparison of benchmarking configurations
Session
- Wednesday, 15 May 14:55 - 15:20
- Room: Session 1 | Las Palmas I
Code size and performance are tracked by the Linaro Toolchain CI for many compiler configurations (GCC/LLVM, O3/O2/Os/Oz, LTO, ...). While this is mainly done to detect compiler regressions, the size and performance figures collected on similar machines can also be used to compare these configurations. Some of these comparisons will be shown during this presentation, such as GCC vs LLVM, Os vs Oz vs O2 vs O3 or LTO vs non-LTO.
Engineer at Linaro
Software Engineer at Linaro
MAD24-322 What does it take to ease SCMI development and testing
Session
- Thursday, 16 May 14:20 - 14:45
- Room: Session 2 | Tenerife I
With the increasing adoption of SCMI by partners and the extensive enablement work carried out by Linaro, the SCMI ecosystem can now be deployed in a number of different configurations across a wide variety of platforms; as a consequence the approach to testing and the ease of developement play a crucial role in delivering a reliable and high-quality SCMI stack implementation. This talk will at first, quickly, address the current and work-in-progress state of the testing and development infrastructures available in the SCMI kernel stack, looking at the perspective and needs of both the SCMI platform server firmware and the SCMI agents, especially focusing on the Linux Kernel SCMI agent. After having laid out such a panoramic view of the existing SCMI development and testing scenarios, the focus will shift on the residual criticalities of current SCMI development process to discuss possible further enhancements to ease development and testing.
Linux Kernel Developer at Arm
MAD24-102 Kernel hacking setup - ARM64 Qualcomm compute platform
Training
- Tuesday, 14 May 14:35 - 15:00
- Room: Session 1 | Las Palmas I
A walk through setting up Qualcomm compute platforms in order to be able to boot to full Debian via fastboot EFI app chainloaded from grub. All steps starting with setting up the proper rootfs using Linaro provided Debian rootfs images, then repacking the Debian initrd with modules and firmware, all the way though setting up grub and fastboot EFI entry to be able to do kernel development rapid testing.
Software Engineer at Linaro
MAD24-108 Lulling your Dragon to sleep - Low Power Modes on linux-arm-msm
Session
- Tuesday, 14 May 15:55 - 16:20
- Room: Session 1 | Las Palmas I
Qualcomm Snapdragon SoCs feature a rich and complex power management architecture, which maximizes frequency and power control of each sub-component. Nearly nothing is connected directly to fixed clock or power sources. This can achieve outstanding performance/power ratios, but also brings some software implementation challenges. In this talk, Konrad will describe how Qualcomm’s power management model affects the upstream kernel today. He will highlight some of the biggest outstanding issues, and outline the end-user experience impact. He will also present ways to rectify these problems that could improve power savings while retaining system snappiness.
Intern Engineer at Linaro
MAD24-329 Developing and Deploying Software for Hybrid Systems
Session
- Thursday, 16 May 16:20 - 16:45
- Room: Session 1 | Las Palmas I
Hybrid systems, composed of diverse compute elements within a single System-on-Chip, enable developers to provide functionality using the most efficient hardware/software combination for different parts of a workload. An example hybrid system may contain a number of application processors running Linux alongside a real-time processor running a real-time operating system and an accelerator for machine-learning inference tasks. Developing software for the different parts of such a system involves using separate toolchains and flows. Deploying the software may also require separate mechanisms for each of the compute elements. In this talk: We look at the current state-of-play for the development and deployment of software using the i.MX8M MINI from NXP as an example platform. We describe our proof-of-concept solutions to solve some of the gaps that we found. We highlight ongoing work in the Linaro community (System Device Tree and OpenAMP) that could improve the overall process of development and deployment for hybrid systems.
Principal Software Architect at Arm Ltd
MAD24-400K2 Boost Arm Ecosystem with openEuler: Ushering in a Future of Digital Intelligence
Keynote
- Friday, 17 May 09:30 - 10:00
- Room: Keynote | Zaragoza III+IV
As the OS platform offering the most comprehensive support for the Arm ecosystem, openEuler has flourished into a thriving community, securing a significant market share. Its all-encompassing design philosophy aligns seamlessly with Arm's extensive coverage across all scenarios, spanning from device to cloud. With a strategic focus on server and cloud environments, openEuler is dedicated to cultivating a full-stack Arm optimization ecosystem. In the realm of embedded systems, the MICA-based embedded platform anticipates future trends in embedded system development. Moreover, openEuler has been steadfastly advancing in the realm of AI, with the AI for OS platform system based on EulerCopilot steadily maturing. Additionally, openEuler spearheads innovative projects in AI optimization. This speech serves as a comprehensive overview of openEuler's progress, technical architecture, and collaborative initiatives within the Arm ecosystem.

Executive Director at openEuler Community
MAD24-328 Recent implementations/refactoring in TF-A
Session
- Thursday, 16 May 16:20 - 16:45
- Room: Session 2 | Tenerife I
Will mainly be covering following aspects - Context Mgmt and memory optimisation to scale for 4 world systems - Exception handling (KFH/FFH) - Firmware Handoff spec and implementations - Feature detection mechanism - ARCH_MAJOR/MINOR and how platforms can adopt it - UNDEF injection support

TF-A developer and maintainer, leading runtime aspects of TF-A (BL31) at arm
MAD24-107 Optimizing suspend/resume
Session
- Tuesday, 14 May 15:10 - 15:35
- Room: Session 1 | Las Palmas I
Optimizing suspend/resume time makes a significant difference for UX and power savings. Especially for wearable devices which typically have small CPUs and small batteries. This talk will point out all the gaps I've found so far and what we could do to address them and some of my TODOs to get there. * Optimizing global async suspend/resume * Using runtime PM to avoid resume/suspend work for short wakeups. * s2idle with older PSCI calls?
Software Engineer at Google
Attested TLS workshop
Linaro Data Center Group steering committee meeting
MAD24-104 Growing your project via Arm Developer Program resources and expertise
Session
- Tuesday, 14 May 14:35 - 15:00
- Room: Session 3 | Tenerife II
The Arm Developer Program is helping Arm experts connect with Arm developers to learn and share information about software development on Arm. Discover how the program’s ambassadors are using their knowledge to expand their skills, grow their network, and shape the future of Arm. Meeting fellow developers is a great way to get involved in and expand open-source projects, or to find your next career opportunity. Discover tips for raising the profile of your work and making a bigger impact. This could mean contributing community content by publishing Arm Learning Paths on learn.arm.com, a community project to share tutorial content with other developers. Learn how you can exploit opportunities to speak at conferences, create videos, write blogs, and attend events to promote your software development expertise on Arm.

Senior principal and distinguished engineer at Arm
ONELab - IoT Advisory council meeting
LEDGE-SC
ONELab Workshop
openEuler meeting
MAD24-222 You would have the bank migrated to cloud before a full-stack secure edge application
Session
- Wednesday, 15 May 15:45 - 16:10
- Room: Session 3 | Tenerife II
As security has always been a important topic for developers to address, but with more and more connected device, security becomes even more complex and something that has to be address further up in the application stack, but in the developer tooling. Much of this tooling and Cloud-Native principles have over time matured in cloud applications. But for edge application developers, this hasn't modernised and remains quite scattered, a broken experience and his disconnected implementation often means the end solution is not secured sufficiently - The State of building a Secure IoT use case on ARM SystemReady
CTO at 56K.Cloud
MAD24-111 *FreeBSD : Training the demon on arm64*
Session
- Tuesday, 14 May 16:30 - 16:55
- Room: Session 1 | Las Palmas I
This talk covers about FreeBSD, an architecture agnostic Open Source distro and the advent of its enablement story in the Arm Open source group. FreeBSD is a standards compliant, Unix-like OS, enjoying a strong hold in the gaming Market, with its competitive strengths on flat, collaborative structure, excellent documentation and ease of use with the permissive license . Building on these strengths, the session dives deeper into the Arm software-led FreeBSD Roadmap with short term goals on core feature support – security, virtualization and Telemetry across commercially viable platforms and long term insight into gap analysis and futuristic planning to align the FreeBSD story closer with arm64 architecture evolution. Finally, the talk concludes with the advantages, myths and challenges around FreeBSD usage and the forward looking strategy not just to establish feature parity with Linux but also to leverage growth opportunities across different market segments.
Software Product Manager at Arm
MAD24-200K2 Accelerating Edge AI Innovation
Keynote
- Wednesday, 15 May 09:20 - 09:40
- Room: Keynote | Zaragoza III+IV
As the common denominator in IoT, Arm architecture is taking a leadership role in enabling a transformative journey towards edge computing and scaling the AI and ML edge opportunity. John explains Arm’s plans to be at the forefront of growth in IoT as the edge AI ecosystem consolidates on Arm. With the recent launch of Ethos-U85, the Ethos NPU family, sits alongside the highly successful Helium Cortex-M instruction set, delivering the highest performance and efficiency for ML workloads. John also explores how the Corstone reference design platform is enabling faster time to market for our most innovative partners and offers a holistic approach to differentiated IoT design, delivering rapid innovation to provide ever richer hardware diversity and optimal performance for the widest variety of edge use cases. Finally, addressing the challenges of deploying AI and ML across such device diversity, John presents some of the software solutions and common standards that are removing the friction from deployment, enabling the product lifecycle support for underpinning regulatory compliance alongside rapid growth.

Senior Director, Software & Ecosystems, IoT at Arm
Meeting with Snap
Meeting with Snap and Qualcom
ISP Work - Next step
MAD24-224 Implementing an Openchain compliant policy and best practice at Linaro
- Wednesday, 15 May 15:45 - 16:45
- Room: Session 2 | Tenerife I
What are the advantages of integrating an Open Source and IP policy into a CI/CD system? How can the software and other IP licenses conundrum be solved and safely comply with the requirements and conditions of upstream Open Source licenses? Can I obtain a software bill of materials which I can use to comply with some of the requirements of the Cyber Resilience Act? Based on our experience providing this kind of service for the Eclipse Oniro operating system ‒ to the benefit of the adopting ODM's from the ecosystem ‒ we will provide a high-level overview of the required effort, potential timeline, potential stumbling blocks and relevant methods. .

Partner at Array

Partner at Array
MAD24-225 An Arm laptop project conclusion
Session
- Wednesday, 15 May 16:20 - 16:45
- Room: Session 3 | Tenerife II
What would it take to run mainline Linux on an Arm laptop built for Windows? That was the question Linaro set out to answer in a project funded by Arm. A bit more than a year later, the Lenovo ThinkPad X13s could be used as a daily driver while running mainline Linux without any out-of-tree patches on top. This talk will give an overview of how this project came about; discuss some of the difficulties encountered, how they were addressed and what remains to be done; and provide a closing summary of the Arm laptop project.
Linux kernel developer at Hovold Consulting
Attested TLS is a proposed extension of the TLS protocol that aims to provide remote attestation for Trusted Execution Environments (TEEs). TLS is a widely used security protocol that has a broad range of applications, from securing connections to HTTPS websites to critical infrastructure networks. The Attested TLS extension would enable secure communication while also verifying the integrity and trustworthiness of the peer TEEs. This workshop will focus on discussing the Attested TLS draft proposal, along with its proof-of-concept implementation that is presently being developed by the Confidential Computing Consortium (CCC). While everyone is welcome to attend, please note that this will be a technical discussion that assumes some prior knowledge of the subject.
- Thursday, 16 May 13:45 - 16:45
- Room: Session 3 | Tenerife II
Fujitsu LLVM
Fujitsu Linaro CI/Benchmark CI
Fujitsu CCA
Fujitsu Forge
SCMI sync meeting
TrustedFirmware Meet and Greet
China Staff Meeting
Linaro Windows Group SC
- Thursday, 16 May 17:00 - 18:00
- Room: Keynote | Zaragoza III+IV
LEDGE engineering
QECO Meeting
Reserve
Reserve
LCG-SC Meeting
Common Repo Alignment
Windows Perf team sync
openEuler meeting with Arm & Linaro
MAD24-300K1 Open Source Under Threat
Keynote
- Thursday, 16 May 09:00 - 09:25
- Room: Keynote | Zaragoza III+IV
Why do we think open source has won? If it has won what has it won? What is the impact of winning? What are the challenges being faced? Is the future of open source under threat? This talk will contextualise these and many other questions and challenges around open source and consider how we might ensure that open source software has a bright and rosy future ahead… and the consequences if we fail to do so.

CEO at OpenUK
MAD24-200K1 Pioneering Edge AI Platforms
Keynote
- Wednesday, 15 May 08:55 - 09:20
- Room: Keynote | Zaragoza III+IV
Join Sergi as he unveils the critical elements and diverse challenges of building a robust Edge AI platform. What defines a successful platform, and what functionalities are crucial for its seamless operation? This keynote will dive deep into the technical foundations and forward-thinking strategies at the core of Edge Impulse, showcasing among others the meticulous testing processes that ensure reliability. Sergi will also illuminate both past triumphs and the future landscape of challenges—some surprisingly non-obvious—and explore the innovative solutions crafted to boost performance and scalability in Edge AI technologies.

SVP Engineering at EdgeImpulse
Arm/Linaro CCA/DCAP alignment
WoA Team Sync
Forge SDL
KWG and Google LT sync
LTS Product Meeting
Board Meeting
Engineering and Services Sales Meet
TBD
PM Team Sync
PM Sync
CodeLinaro Product Review
ONELab Week followup
CLO Weekend Support
ONELab Engineering meeting
Team sync up and brainstorming (Lei Zhou)
CoCo Catchup
CoCo/Veraison Catchup
ARM Performance Project
fTPM Discussion
LCG Private meeting
AVF - virtio discussion
LEDGE - virualization - QEMU - QCLT - QC Sync
Array/Linaro
AOSP CTS Tradefed Memory Footprint and Arm compatability
LEDGE assignees + employees syncup
A single strategy for our future
OneLab Catchup
OpenAMP Sync
Cassini Discussion
Qualcomm LT and KWG Sync
sync up with Bjorn
WebDev meeting
SPIRE & ONELab
Kaly/Mike 1:1
Chat about the sales sprint June 3-4
gs101 / exynos sync
VLT Team Meeting
Common repo pre-discussion
VLT Sync
Chat about working scope
ONELab security
Common Repo Discussion Part II
Virtualization huddle
Meet Sandeep
UEFI Discussion
Syncup
Libcamera SoftISP
AudioReach OSP Strategy
- Wednesday, 15 May 13:30 - 15:30
- Room: Other Venue |